Friday, February 27, 2009
Ek Din Aap Yoon Humko Mil Jayenge-YESS BOSS
Phool Hi Phool Raahon Mein Khil Jayenge
Maine Socha Na Tha
Ek Din Aap Yoon Humko Mil Jayenge
Phool Hi Phool Raahon Mein Khil Jayenge
Maine Socha Na Tha
Ek Din Zindagi Itni Hogi Haseen
Jhoomega Aasmaan Gaayegi Ye Zameen
Ek Din Zindagi Itni Hogi Haseen
Jhoomega Aasmaan Gaayegi Ye Zameen
Maine Socha Na Tha
Dil Ki Daali Pe Kaliyaan Si Khilne Lagin
Jab Nigaahein Nigaahon Se Milne Lagin
Dil Ki Daali Pe Kaliyaan Si Khilne Lagin
Jab Nigaahein Nigaahon Se Milne Lagin
Ek Din Is Tarah Hosh Kho Jayenge
Paas Aaye To Madhosh Ho Jayenge
Maine Socha Na Tha
Ek Din Aap Yoon Humko Mil Jayenge
Phool Hi Phool Raahon Mein Khil Jayenge
Maine Socha Na Tha
Jagamagati Hui Jaagti Raat Hai
Raat Hai Ya Sitaaron Ki Barsaat Hai
Jagamagati Hui Jaagti Raat Hai
Raat Hai Ya Sitaaron Ki Barsaat Hai
Ek Din Dil Ki Raahon Mein Apne Liye
Jal Uthenge Mohabbat Ke Itne Diye
Maine Socha Na Tha
Ek Din Zindagi Itni Hogi Haseen
Jhoomega Aasmaan Gaayegi Ye Zameen
Maine Socha Na Tha
Ek Din Aap Yoon Humko Mil Jayenge
Phool Hi Phool Raahon Mein Khil Jayenge
Maine Socha Na Tha
Maine Socha Na Tha
Maine Socha Na Tha .
"Roz Kii Taraah Aaj Bhii Taare
Subha Kii Gard MeiN Naa Kho JaayeiN
Aa ! Tere Gham MeiN Jaagtii AankheiN
Kam Se Kam Aik Raat So JaayeiN."
Wednesday, February 25, 2009
Fear not that you might make a mistake in believing your dream
Fear rather that if you don’t go for it
You might stand before God and he’ll tell you
You could have succeeded had you had a little more faith
Fear not that you might fail
Fear rather that you will never succeed
If you never try and if you are unwilling to take risks
Fear not that you might get hurt
Fear rather that you will never grow
If you wait for painless success
The old man said to the young man,
“Why not go out, on a limb,
After all is not that where the fruit is”
Monday, February 23, 2009
JAI HO : Rahman regales the world, gets India 2 Oscars

It was the day of the Slumdog at the Oscars!
Out of the ten Oscars that it was nominated for, Slumdog Millionaire swept eight Oscars, which included two Oscars for music maestro A R Rahman, Best Director for Danny Boyle and Best Sound Mixing for India's Resul Pookutty.
The film opened its Oscar account by winning in the Best Adapted Screenplay category for Simon Beaufoy.
After that, there was no looking back as the film went on a dream run to win awards in Film Editing for Chris Dickens, Best Cinematography for Anthony Dod Mantle and Sound Mixing for India's Resul Pookutty.
36-year-old Resul Pookutty created history by becoming the first Indian to bag the Oscar for Best Sound mixing. Pookutty shared the Oscar with Ian Tapp and Richard Pryke for their collaborative work for the film
"This is unbelievable. I share this stage with two magicians...I dedicate this award to my country," Pookutty said while accepting the award.
The biggest success for India came with a double Oscar treat for Rahman for Best Original Music Score and Best Song (Jai Ho).
The composer was overwhelmed and interspersed his speech with Hindi as well as Tamil on receiving the coveted trophy here Sunday.
"There is a dialogue from an old Hindi film - "Mere paas ma hai" - which means I have nothing but a mother. My mother is here, I have her blessings. I am glad she could be here," said Rahman.
He ended the acceptance speech by saying "God is great" in Tamil, something he says after winning every award.
He shared the second Oscar for best original song for the film's theme number Jai Ho with noted Indian lyricist Gulzar.
"All my life I had a choice between hate and love. I chose love and I am here," said Rahman after receiving his second golden statuette.
British filmmaker Danny Boyle won the Best Director award. Boyle was visibly excited and overwhelmed as he said "I want to thank my dad, my sisters and my wife... one person we haven't thanked is the choreographer who directed the last song in the film - Longines. I want to thank him too," said Boyle after receiving the award.
The film also won an Oscar for Best Motion Picture. The announcement for Best Picture saw a jubilant cast and crew of the film, celebrating together on the stage.
Celebrating MahaShivRatri | Om Namha Shivay

Lord Shiva is considered as one of the three main Deity [ त्रिदेव: The three forms of God – Brahma (creator), Vishnu (sustainer) and Mahesh or Shiva (destroyer) ] of Hindus. Aadi Shankaracharya has written quite a few stotras (songs of worship) on Lord Shiva. Many known and unknown scholars have also expressed their adoration for Lord Shiva with their own poetic verses. However among all stotras or stutis, the one written by Pushpadanta became very popular.
It would be interesting to know the circumstances which led Pushpadanta to compose this great song. Pushpadant was a Gandharva (गांधर्व - musician in the court of Indra). He had a particular liking for flowers. It so happened that he saw beautiful garden adorned with charming flowers. It was King Chitraratha’s royal garden. King Chitraratha was a devotee of Lord Shiva. Every day, he used to offer flowers from his palatial garden as a symbol of his devotion to Lord Shiva.
Pushpadanta was fascinated by those stunning flowers, so he began to steal them. As a consequence, king Chitraratha was unable to pick flowers for offering to Lord Shiva. It was not an isolated incident. It became a routine affair. King Chitraratha made every effort to address the issue but remained unsuccessful. The reason was very simple; Pushpadanta had divine power to remain invisible.
At last, King spread Bilva leaves (बिलीपत्र), considered auspicious offering to Lord Shiva in his garden. Pushpadanta, unaware of this sudden change, stepped on Bilva leaves and incurred Lord Shiva’s wrath. Shiva punished him for his misdeed and Pushpadanta lost his divine power of invisibility.
In order to seek absolution and please Lord Shiva, Pushpadant created a stotra (song of praise) in which he elaborated at length upon Shiva’s greatness. Shiva was pleased with the hymn, absolved him and returned his divine powers. The very stotra became known as the 'Shiva-mahimna Stotra'.
The recital of this stotra is very beneficial as proclaimed by one of its verses:
अहरहरनवद्यं धूर्जटेः स्तोत्रमेतत् ।
पठति परमभक्त्या शुद्धचित्तः पुमान्यः ॥
स बवति शिवलोके रुद्रतुल्यस्तथाडत्र ।
प्रचुरतर धनायुः पुत्रवान्कीर्तिमांश्च ॥
“Anyone who recites this hymn with a pure heart and devotion will be blessed with fame (कीर्ति), wealth (धन), long life (आयु) and many children (सुत) in this mortal world, and will attain Kailas, Shiva’s abode, after death.”
दीक्षा दानं तपस्तीर्थं ज्ञानं यागादिकाः क्रियाः ।
महिम्नस्तवपाठस्य कलां नार्हन्ति षोडशीम् ॥
“Benefit of singing Shivmahimna stotra is far greater than either the benefit of spiritual initiation (दीक्षा), charity (दान), austerity (तप), pilgrimage (तीर्थ), knowledge of the scriptures (ज्ञान), or the performance of ceremonial sacrifice (यज्ञ-याग).”
Shivmahimna Stotra has 43 verses in Sanskrit. For the benefit of Gujarati people, Shri Yogeshwarji has translated it into simple and easy-to-understand Gujarati language.
It is interesting to know that Gujarati translation of Shiv Mahimna Stotra was completed by Shri Yogeshwarji in the year 1949. When Yogeshwarji first visited Amarnath – the famous pilgrim place of Lord Shiva in 1951, he offered this stotra to Lord Shiva along with ‘Amarnath Stuti’ and was blessed with the divine vision of the Lord.
Ashit and Hema Desai - famous Gujarati singer duo composed an audio album entitled ‘Vande Sadashivam’ containing Yogeshwarji’s poetic rendering of Shivmahimna Stotra in Gujarati. The album also contains immensely popular Shiv Stuti and Amarnath Stuti, also written by Yogeshwarji.
Here we have presented Gujarati translation and Hindi along with Sanskrit verses for the benefit of our readers. It is also accompanied by mp3 audio of the Gujarati verses by Ashit and Hema Desai. We hope that our visitors will be delighted by this offering.
Thursday, February 19, 2009
Soniyo o Soniyo (Lyrics) Raaz-2
Baby, come stand by my side
Come and be my guiding light
Oooo… I’ll be what you want me to be
I’ll give all my love in whole of my life
Soniyo, o soniyo
Tumhe dekhta hu to sochta hu bas yahi
Tum jo mera saath do, saare gham bhulake
Jee lu muskuraake zindagi
Tu dede mera saath thaam le haath
Chahe jo bhi ho baat, tu bas de de mera saath
Tu dede mera saath thaam le haath
Chahe jo bhi ho baat, tu bas de de mera saath
I get this feeling now, I cannot wait no longer
I know your love will keep me happy
Will keep me stronger
I get this feeling now, I cannot live without you
I know your love’s the only one so true
Raho me, tanha hu saath le chal yu
Sang tere safar poora karu
Raho me, tanha hu saath le chal yu
Sang tere safar poora karu
Kya kahu ae zindagi
Tu hai meri saans, rehna tu paas har ghadi
Tu dede mera saath thaam le haath
Chahe jo bhi ho baat,
Tu bas de de mera saath,
Tu bas de de mera saath
Tujh ko jo, paaya toh hai yeh lagta kyu
Baho me bas teri mehfooz hoon
Tujkh ko jo, paaya to hai ye lagta kyu
Baho me bas teri mehfooz hoon
Tum bano, saaya mera, zindagi mein aao
Zindagi bitaao bas yahi
Tu dede mera saath thaam le haath
Chahe jo bhi ho baat
Tu bas de de mera saath
Tu bas de de mera saath
Baby, come stand by my side
Come and be my guiding light
Oooo… I’ll be what you want me to be
I’ll give all my love in whole of my life
Baby…. Come and be my guiding light
Movie Name : Raaz 2- The Mystery Continues
Music Director : Raju Singh
Lyrics : Sayeed Quadri
Starring : Adhyayan Suman, Emraan Hashmi, Kangna Ranaut
Director : Mohit Suri
Producer : Mukesh Bhatt
Song Title : Soniyo
Year : 2008
Tagged with: 2008, Adhyayan Suman, Emraan-Hashmi, Kangna-Ranaut, Mohit-Suri, Mukesh-Bhatt, Raaz 2- The Mystery Continues, Raju Singh, Sayeed-Quadri, Soniyo, The Mystery Continues
Wednesday, February 18, 2009
How to find out if your computer has a virus
An easy to understand introduction to computer viruses and malicious software with guidance on detecting, removing and preventing infection.
Aimed mainly at people who use Microsoft Windows.
If you use the Internet, your computer is at risk of infection from viruses. Much like biological viruses, some are harmless, some are merely annoying and some can make your life hell. Even if you only occasionally use your home computer, it is important that you understand the risks and know how to protect yourself.
What is a virus?
Why do people make viruses and other malware?
Stealing your bank details
Your bank will have warned you that shopping on the Internet involves a risk of people stealing your financial details. This can result either from inadequate security considerations by the online seller or because you have some form of malware on your computer. This is a scary thought when you consider that certain transactions can take money from your account immediately if the criminal has access to the right details.
Stealing your identity
Even if you don't shop online, you could potentially end up in a lot of difficulty if someone steals your identity. Many websites request that you provide them with personal details that may seem innocuous enough, but to criminals can provide the first step to identity theft. A gradual accumulation of your personal details collected by malware could be sufficient to enable someone to build up a profile of your identity and, for example, apply for credit in your name. You might not find out about this until the credit company has started hassling you for the repayments.
Using your computer for illegal activity
Have you ever wondered where all those spam e-mails come from offering investment tips, cheap viagra and breast enlargemnts? One way that spammers get junk mail delivered is to send it using software, known as bots, running secretly on other people's computers. With millions of computers connected to the Internet, malware that uses innocent home users' equipment for dubious or illegal activities can put a lot of power in the hands of deviant people.
Find out if you're infected
Antivirus software
1. Manually air gap the computer
Disconnect your computer from the Internet immediately, preferably physically (i.e. disconnect your modem or network cable).2. Download antivirus software from a trusted source using a clean computer.
Use a computer that is already running up-to-date reputable antivirus software to download the latest antivirus installation software, then burn the installation files CD or DVD. If you don't want to pay for antivirus software, some antivirus companies offer free antivirus software for home use. Make sure you download from a source that has a reputation for virus free downloads such as www.download.com. Avast! Home Edition and AVG Antivirus Free Edtion are two popular antivirus products that are free for home use, easy to download and easy to install[2].If downloading and burning isn't possible or seems too complicated you're probably going to have to buy some software from your local computer shop. There are many commercial antivirus products available off-the-shelf for home use. Ask the dealer which product will suit you best.
3. Stop suspicious software from running
Kill any processes that are running that you suspect may be malware. To do this, bring up Task Manager (by pressing Control, Alt and Delete at the same time and then clicking on Task Manager) then look through the list of processes on the processes tab. Make a note of the names of all the processes, then using an uninfected computer, look up the names of these processes on a reliable site like http://www.processlibrary.com/. If possible, manually stop any unidentified or malware processes on the infected machine using the End Process button from Task Manager. You should also try to stop any unnecessary or suspicious applications from running using the End Task button on the Applications tab in Task Manager. Leave your computer running in this condition as malware is likely to restart if you restart the infected computer.4. Backup your data
Backup your important personal files to CD, DVD or another form of removable media. Beware that these files may contain infected material so put a warning label on the disk. These backups are for an emergency restore only, such as if the files on your hard drive are wiped unintentionally later on in the procedure or if the antivirus installation prevents the computer from starting correctly.
5. Install antivirus sof tware and scan for viruses.
It is preferable to install the antivirus software in a diagnostic mode such as safe mode in Microsoft Windows[3]. Malware and extraneous operating system services are less likely to be running on you computer if you are in safe mode, hence it is less likely that the installation can be sabotaged or conflict with another program. Not all antivirus programs will allow you to perform an install in safe mode. In that case, at least make sure that suspicious and unneccesary processes are not running by following the instructions in Step 3 before installing the antivirus software.Follow the instructions supplied by your antivirus software providor to complete the installation. This will usually involve restarting the computer and automatically retrieving the latest antivirus updates from the Internet.Once you have completed the installation you should use the software to run a scan of your computer. Depending on the age and type of your setup this may take hours, so have patience. Once the scan is complete your antivirus software should present you with some reassuring information - either that the machine is clean or that malware has been detected that can now be bannished. The exact procedure will vary depending on your antivirus software.Make another backup of the now (hopefully) clean personal data files to CD or DVD. If you are intending to or have to do a low-level reinstallation (see Advanced Techniques), use these backups to restore your personal data rather than those you made in step 1.
6. Get advice on identity theft.
If you suspect that you may have been the victim of malware you need to prepare for the possibility that your identity has been stolen. Advice may vary depending on your country, but a good starting point will be contacting your bank. You may need to renew accounts and cards or even file a police report. In all cases you must keep a close watch on any future bank statements. Advice in the UK is available from the Home Office online: http://www.identity-theft.org.uk/what-if.html. In the USA, the Department of Education provides similar advice at http://www.ed.gov/about/offices/list/oig/misused/index.html.
Isn't there a faster detection method?
- Computers mysteriously shutting down on their own.
- Programs running excessively slowly.
- Unfamiliar processes running on the computer.
- Unfamilar programs starting on their own or duplicating themselves.
- Other unexpected computer behaviour.
How do you get a virus?
The Blaster worm
Blaster was a malicious program that spread itself over the Internet to Windows XP and Windows 2000 computers in 2003. One of the syptoms was quite dramatic, effectively making a computer unusable by forcing it to shut down within seconds of booting up. Most of the high profile viruses in the recent years up until then had spread through email attachments and required a bit of assistance from the user themselves, but Blaster could spread over a network without the user being involved. Computers without the latest Windows updates or the protection of a firewall were vulnerable merely by being connected to the Internet.
Phishing sites
Your bank has probably warned you about phishing (pronounced 'fishing') sites. Users are directed to the phishing site from a phishing email - a bogus but official looking electronic communication pursuading you to visit the phishing site. By presenting a web page that looks identical and could even appear to have the same URL as a familar trustworthy site, such as your online bank, the phishing site lures you into following instructions or submitting information in the belief that you are safe, when in fact you are submitting information to a criminal or assisting them with the installation of malware on your computer.A variation on this idea is that gaining the victim's trust by appearing that you are there to help them with an urgent problem. Some malicious webpages disguise themselves as a warning messages claiming that you have a virus but that it can be removed by following certain instructions. Those instructions then acheive the exact opposite - exposing the computer to an attack and installing the malware.Auto run from CDs, DVDs and pendrives
The PC's autorun or autoplay feature was once very useful as it enabled you to insert a disk, such as a data CD, and the software on the disk would start automatically. As long as you only inserted media that came from a reputable source, you could be pretty sure that this feature wasn't going to automatically run any malware because in the old days, CDs read only for most users, so malware was not able to write itself to the disk media in the first place.Today most users have CD or DVD burners and can use pen drives (also known as 'USB sticks' or 'memory sticks'). Although lots of CDs and DVDs are still read only, pen drives are almost always the opposite. With the autorun feature still enabled on most computers, malware can easily install itself to and from pen drives that are inserted into your computer. You can stop autorun from functioning by holding down the shift key while you insert the pen drive or CD. To disable the feature more permanently is a bit more complicated, but instructions are provided in a Microsoft knowledge base article available from http://support.microsoft.com/kb/953252.The unprotected transfer of data with pen drives is so prolific at the moment, it is suspected malware has even managed to make its way onto the International Space Station using this method [5].
Staying protected
- Always have antivirus software installed and up to date. Check for web browser and OS updates regularly.
- Use 'strong' passwords and don't reveal them to anyone. See http://www.microsoft.com/protect/yourself/password/create.mspx for password advice.
- Don't use an administrator account if you don't have to. Most modern operating systems support accounts with different levels of privelege. If you're just surfing the web, you don't need to be logged on as the system administrator and your normal user account doesn't need administrative priviledges.
- Verify the authenticity of websites and emails that request information. Check that the webpages and emails come from the company they claim to be and are not a clever typographical variation on the company name. Be suspicious of any email requesting personal or financial information and ignore all spam mail.
- Don't download or install software from an untrusted source and hold down the shift key when inserting pen drives or other types of media.
- Use an e-mail service that scans emails for malware and don't open email attachments from an untrusted source, even if apparently forwarded by friends.
- Use a personal firewall. Most commercial home operating systems now come with a free firewall built in. If not, use a third party personal firewall product designed for your operating system.
- If while browsing the Internet you start to receive messages claiming that you have a virus, exit your web browser, disconnect from the Internet and restart your computer. Once restarted, if you genuinely have a malware problem, your antivirus software will inform you after downloading the latest updates and doing a scan.
- Be suspicious of instuctions from unverifiable sources. If an someone tells you to manually adjust the configuration of your computer, find out what the risks are and try to understand what your browser configurations actually do[7]. Never assume that an unverified source is an innocent source because it has plausible motives. A plausible positive motive is exactly what malicious attackers use as their disguise.
In general you should be vigilant regarding computer security and not just where it concerns malware. If personal or financial data needs to be kept secret then it must be sent using a secure web page. This is usually signified by an address starting with 'https' instead of 'http' and a symbol presented by the web browser (not the webpage) such as a padlock. Find out exactly what this should look like in your web browser so you don't fall for fakes and remember that this is only protecting the information in transit, you still need to be sure that the recipient is trustworthy. Also, be aware that a standard e-mail is not a secure private communication - the data is very easy to read in transit by someone snooping with the right equipment. If you do send payment details over the Internet use a credit card. Credit cards are less risky than debit cards as the seller does not receive immediate payment, so you may have time to cancel the transaction if you realise that you're being ripped off.
Advanced malware removal
Re-installation
This may seem like overkill, but re-installation is the most reliable way to get rid of a virus. The lower the level at which you can do this the better, because the aim of some malware is to entrench itself at as low a level as possible. So if you know how, format your hard drive, then re-install the OS with current anti-virus before restoring your applications and data. Obviously you are in a better position to do this if you are pre-prepared. Sometimes when you buy your computer it will come with a restoration disk that can be used to return the machine to its factory condition. Keep this safe. If not, find out from the manufacturers/suppliers if your computer has an alternative factory restoration method, and if not, look in to preparing your own restoration procedure.
Malware removal tools
Specific malware often needs a specific removal tool in addition to the standard antivirus software. These can often be obtained for free from antivirus companies. Semantec, for example, provides a list of recent removal tools at http://www.symantec.com/business/security_response/removaltools.jsp.
Recent improvements from Microsoft
Some jargon explained
Notes
The highest paid CEOs in India

Even in these times of economic gloom, there are chief executive officers who are earning huge salaries. Some time ago, Prime Minister Manmohan Singh had sparked off a debate when he suggested that CEO salaries should be curbed. That was when there was no economic crisis anywhere in sight.
Now even the epitome of capitalism, the United States, has endorsed those views, and American policymakers want CEO compensation to be kept at manageable levels. Meanwhile, here is a list of the highest paid CEOs in India.
Note: Market cap as on February 16, 2009
Mukesh D Ambani
Rank: No 1
Designation: Chairman and managing director
Company: Reliance Industries Ltd
Compensation: Rs 44.02 crore (Rs 440.2 million)
Reliance market cap: Rs 193,076.66 crore (Rs 1930.77 billion)
Background: Mukesh Ambani has been ranked India's richest person, and the world's fifth richest man, by business magazine Forbes. His net worth is approximately $50 billion. With a personal stake of 48 per cent, he is the largest shareholder of Reliance Industries, India's largest private sector enterprise.
Ambani, who joined Reliance in 1981, led the creation of the world's largest grassroots petroleum refinery at Jamnagar, Gujarat, built at a cost of Rs 100,000 crore (Rs 1,000 billion).
His fortune has seen a 62 per cent drop since January 2008, but he still ranks No 3 in Forbes' list of world's wealthiest CEOs.
Saturday, February 14, 2009
Sonu Nigam (Niigaam) top Romantic Songs Forever

1. Mere Haath Me Terea Haath Ho. Saari Jannatte Mere Sath ho....
Fana
2. O Soniyo - Raaz 2
3. Tu hi tu satrangi re (Dil se) – 1998 – A. R. Rehman
If you ask me “which is most difficult song sung by Sonu Nigam”, I will name this without thinking for a second. He sung this song with such an ease that
4. Aahista aahista milte hai dil sanam (Yeh Zindagi ka safar) – 2001 – Daboo Malik
Many people would not have heard this song, but this is really one of the best songs that Sonu has ever sung. Most rhythmic part of the song comes when Sonu sings:
“Raaste yeh naye, Inme hum kho gaye….
Manzilon ka pata, Milke dhoondhenge hum ….”
5. Meri jindagi mein aaye ho (Armaan) – 2003 – Shankar, Ehsaan, Loy
Armaan, a flop movie of 2003 with a very good duet in dulcet voices of Sonu Nigam and Sunidhi Chauhan. A slow romantic song which will give peace to your mind.
6. Hamein jab se mohabbat ho gayee hai (Border) – 1997 – Anu Malik
Sandese aate hai.. was the song which became more famous from this movie (Sonu was also a part of that), but this is one song which will make you fall in love (not necessarily with a gal or a boy, might be anything).
7. Kasto maja hai (Parineeta) – 2005 - Shantanu Moitra
This is the song which can make Sonu Nigam proud with one more national award this year. Sonu Nigam used to be the anchor of famous TV show “SA-RE-GA-MA” when Shreya Ghoshal came out as a product of this show and now they make arguably the best singing pair in Hindi Film industry.
8. Saathiya (Title song) – 2002 – A. R. Rehman
Sonu’s magical voice and Rehman’s magical music, what can we ask for in a good song.
9. Fiza (Title song) – 2000 – Anu Malik
The second most difficult song that Sonu has sung (after “Satrangi “). This song has so many ups and downs that singing this song itself is difficult and Sonu has sung it very well.
10. Pehli pehli baar (Sangharsh) – 1999 – Jatin-Lalit
This song is sung in the mellifluous voices of Sonu Nigam and Shraddha Pandit and is one of my all time favorite song. This song has a soothing effect which makes you feel comfortable and whenever I listen to this song I tend to forget all my tensions for some time.
11. Sandese aate hai (Border) – 1997 – Anu Malik
There are no words to desribe this song; I can eloquently say this as the “Best composition by Anu Malik”.
12. Rabba mere rabba (Mujhe kuch kehna hai) – 2001 – Anu Malik
This song has some “Ajeeb si Kashish“, which makes it a very different and very special song. The best part is, when Sonu sings “Is pyaar ko main .. kya naam doon …”.
13. Main hoon na (Title song) – 2004 – Anu Mailk
Sonu Nigam and Shreya Ghoshal are going to break and make many new records in singing, they both are extremely talented and more importantly they are young and they have enough time to reach at their pinnacle. This song is again a perfect example of the two singers’ talent.
14. Jaage jaage (Mere yaar ki shadi hai) – 2002 – Jeet Pritam
The best song of this movie and Sonu Nigam shining in the song despite Udit Narayan and Alka Yagnik also singing the song too.
15. Meri duniya hai (Vaastav) – 1999 – Jatin-Lalit
Many of us would not have expected such a melodious song from a movie like “Vaastav”. Sonu and Kavita Krishnamurthy have sung this song beautifully.
16. Meri duniya mein aake (Tum bin) – 2001 – Nikhil-Vinay
The third most difficult song that Sonu has ever sung..?? Yes the third most difficult and a beautiful song to listen.
17. Suraj hua Maddham (Kabhi Khushi kabhi gham) – 2001 – Sandesh Shandilya
One of the best compositions of Sandesh Shandilya and Sonu Nigam and Alka Yagnik singing the song to perfection.
18. Kal ho na ho (Title song) – 2003 – Shankar, Ehsaan, Loy
This is one of the songs that Sonu Nigam finds very close to himself, so there’s nothing else to write about this song.
19. Gustaakh dil tere liye (Dil maange more) – 2004 – Himesh Reshmmiya
Another good composition from Himesh Reshmmiya and Sonu gave the right energy to this song.
20. Do pal ruka (Veer Zaara) – 2004 – Late Madan Mohan
”Ek Dard bhara geet”, sung with enormous ease and the honeyed voices of Lata Mangeshkar and Sonu Nigam doing the justice with Late Madan Mohan’s composition.
21. Aisa lagta hai (Refugee) – 2000 – Anu Malik
If you are going for a sleep, listen to this song in low volume and you will feel relaxed; the mellisonant voices of Sonu and Alka Yagnik have added magic to the fine composition from Anu Malik.
22. Mujhe raat din (Sangharsh) – 1999 – Jatin-Lalit
A melodious romantic song with Sonu singing to it with too much perfection, Jatin-Lalit (Romantic kings of 90’s) giving one of their one of the best performances, this song is very close to me.
Here are some of my favorite songs from Sonu Nigam’s Albums that I have not added to the 20 songs but the songs are very dear to me.
1. Deewane hoke hum milne lage sanam (Jaan)
2. Ab mujhe raat din (Deewana)
3. Kuch tum socho kuch hum sochein (Deewana)
4. Mohabbat kabhi maine kee to nahin thee (Yaad)
5. Is kadar pyar hai tumse (Deewana)
6. Tera Milna Pal Do PAl ka.. (JAAN)
Another of my fav ...
Dhalne lagi hai raat, koi baat kijiye..(Inteha)
Let me tell you there was a time when one singer used to take hold of the whole industry for years; Kishor Kumar and Mohammad Rafi have done the same for more than 20 years (at least). Now the scenario has changed, people want a new freshness in every new song they listen and hence even the inimitable king of 90’s Kumar Sanu is not getting many songs to sing; in other words singers are not long lasting now-a-days. But I am 200% sure that Sonu Nigam will be on top of all for a long time to come, he still has miles to go before he sleeps.
Happy Valentine's Day | Catch the LOVE !
I think of you often...I do,
From morning 'til evening I do,
When memories bring laughter
Or moments bring pain,
There is faithfulness, too, once again.
And time always shows me
And God always shows me
Both sunshine and rain,
How, we gain yearly
From the love we're share dearly.
So, my dear, my sweet bubbaloo,
Remember our love, dulce bubbaloo,
For we've come so far and there's so much to come
And I have love to yet give
For the life we will live...together.
Make little of what makes you cry,
Be sure that what makes you cry
Has greater desire and a more certain will
To pray for His help from above
and restore the feelings of love.
So let's stir up our passion today,
Let memories give way today,
To the now and the future
For the joys and hopes and for all
 The times my heart hears you call.
The times my heart hears you call.I'm so glad,
I'm so glad,
I love you
You love me fine
Be my Valentine.
Contributed by: Jim
--------------------------------------------------------------
My Valentine
Valentines is near
Just wishing you were here
You will always be near
My heart will never be the same
Beneath my skin, my soul lies waiting for you
Everyday I think of you I feel blue
Never give up hope
Remembering the first kiss
All I ask is to be with you
And for you to be my Valentine
For I will always cherish your heart in mine
Contributed by: Jose Villalpando
--------------------------------------------------------------
Love's Philosophy
The fountains mingle with the river
And the rivers with the ocean
The winds of heaven mix for ever
With a sweet emotion;
Nothing in the world is single,
All things by a law divine
In one another's being mingle
Why not I with thine?
See the mountains kiss high heaven
And the waves clasp one another
No sister-flower would be forgiven
If it disdain'd its brother;
And the sunlight clasps the earth,
And the moonbeams kiss the sea
What are all these kisses worth
If thou kiss not me?
Contributed by: Maria
--------------------------------------------------------------

Colors of Love
Love!
Love can be red, like the intense heat of a passionate kiss
.....the color of sweetness
.....the color of strawberries
Love can be blue, like the comfort we take in a pair of denim jeans
.....the color of strength
.....the color of perfect skies
Love can be yellow, bright and warm like the morning sun
.....like the sounds of laughters of children on the merry-go-round
.....like the sounds of fun from the boys flying kites in the open
fields
Love can be green, peaceful and serene I can hear your heart beats
.....it is the feeling of a loving hand that touch a grieving heart
.....it is the whispering of trusting words to a distressing soul
Love can be orange, the loudness of it can drive you up a wall
.....it can drive you to sing like nobody is listening
.....it can drive you to dance like nobody is watching
Love can be purple, the courage we need to love bravely and unselfishly
.....the moment I first kiss you i know that i am not afraid to risk involvement .....the day the declaration of your love for me was made known to the world
Contributed by Arun Kumar
--------------------------------------------------------------
My Love
After so many years of loving you,
After so many things we've been through,
Still I couldn't find the reason,
Tell me why am I in so much love with you?
The day you left me,
My eyes couldn't stop crying.
The day I lost you,
A day didn't go I had pray for dying.
Come back my love,
Someone's still waiting for you.
Come back my love,
Someone will always wait for you.
Joti (Bangladesh)
--------------------------------------------------------------

Friends Forever
Are we friends,
Are we not.
You told me once, but I forgot.
So tell me now and tell me true,
So I can say I'm here for you.
And if I die before you do,
I'll go to heaven and wait for you.
I'll give the angels back their wings,
And risk the loss of everything.
Just to prove my friendship is true,
Just to have a friend like you.
Sadie
--------------------------------------------------------------
You've Touched My Heart
You've given me a reason
For smiling once again,
You've filled my life with peaceful dreams
and you've become my closest friend.
You've shared your heartfelt secrets
And your trust you've given me,
You showed me how to feel again
To laugh, and love, and see.
If life should end tomorrow
And from this world I should part,
I shall be forever young
For you have touched my heart
--------------------------------------------------------------

To My Husband, My Life, My Eternal Valentine
This is to thank you for being by side
For comforting and caring when I was all confused inside.
This is for the phone calls you make every day
Just to tell me “I love you” every minute of the day.
The way you take my hand in yours
For all the world to see
That this is the woman
Who is most special to me.
You always seem to know
When I need a hug, kiss or smile…
You never cease to amaze me
When you say, “I'm here…let's talk for a while.”
In decades past we've had our share
Of ups and downs and problems galore
But you are the one who remained at my side
Never thinking of walking out the door.
I adore the way you tell me,
“You are my forever best friend,”
I love the way I believe in you…
And that you will be there till the end.
Thank you for all the time you give me
And for saying, “It's never enough…”
Thank you for listening as I ramble on…
When things become rather tough.
We are in the best years of our lives
Thirty four years on our journey together
I want to grow old with you…and you with me
I want to love YOU---FOREVER.
JoMarie Grinkiewicz
--------------------------------------------------------------
Rain or Shine ... Be My Valentine
Raindrops on our dresses,
Sunshine on our face,
No matter what the weather,
The look of love won't be replaced.
The silent sound as rain falls,
The brilliance of the sun.
They only promise radiance,
Caused by either one.
Let it rain, or let it shine,
It won't matter none.
You're such a lovely Valentine,
In either rain, or sun.
Let it snow, let it hail,
Earth blanketed with white.
It won't prevent our day,
Or deny the magic of our night.
Donna Wallace
--------------------------------------------------------------

It's More Than Saying I Love You
We give on this day candy and flowers,
But we never stop to say thank you for the many hours.
You have stood by my side and gave a smile,
As if to tell our hearts it's been worth every mile.
No need to buy a teddy bear or even a card,
It's pretty simple and not at all hard.
Just put your arms around me and hold me tight,
And say without words that in your heart all is right.
You may say I Love You throughout the year,
But on this day you need to make sure.
The words so sweet and straight from your heart,
That your life would be lonely without my part.
So put forth the effort and take the time,
Look me in the eye and say I'm glad you're mine.
AngelWatchin
--------------------------------------------------------------
Valentine's Day Love Poems
How Do I Love Thee? Let me count the ways.
I love thee to the depth and breadth and height
My soul can reach, when feeling out of sight
For the ends of Being an ideal Grace.
I love thee to the level of everyday's
Most quiet need, by sun and candlelight.
I love thee freely, as men strive for Right;
I love thee purely, as they turn from Praise.
I love thee with the passion put to use
In my old griefs, and with my childhood's faith.
I love thee with a love I seemed to lose
With my lost saints,--I love thee with the Breath,
Smiles, tears, of all my life!--and, if God choose,
I shall but love thee better after death.
Elizabeth Barret Browning
--------------------------------------------------------------
Mother's Valentine
My mother made a valentine
So very long ago
And decked it out all prettily
Like for a special beau.
I watched her as she cut the heart
Then frilled it up with lace
And worked artistically away,
A smile upon her face.
She wove a ribbon, shiny red,
Among the lace so white
Then placed a picture of herself
Through a slit she cut inside.
I saw the words, “I love you, Dear,
I'm proud to be your wife
You're given me the blessings
Of a blissful, wedded life.”
I felt like laughing out for joy,
My childish heart was glad!
Mom's special valentine would go
To a special beau named Dad.
Lucille King
--------------------------------------------------------------

Valentine Memories
Grandma's book of valentines
Rekindles memory's flame,
Of days when she was just a girl
And life a happy game.
Each lace-edged card a getting bears
From friends of long ago,
Girls in gingham dresses
And that “special” Sunday beau.
It brings a twinkle to her eye,
Dissolving lines of age,
As we sit in the lamplight
And turn each well worn page.
It makes me kind of wonder
f perhaps some distant day,
A grandchild shall sit at my side
And leaf each page this way.
‘Cause I could sit for hours,
There at my grandma's knee,
And listen to the stories
That the valentines set free.
A book of antique valentines
That reaches black in time
To tell the tales of yesteryear
In illustrated rhyme.
Shirley Sallay
--------------------------------------------------------------
To Celia
Drink to me, only, with thine eyes,
And I will pledge with mine;
Or leave a kisse but in the cup,
And Ile not look for wine.
The thirst, that from the soule doth rise,
Doth aske a drink divine:
But might I of Jove's Nectar sup,
I would not change for thine.
I sent thee, late, a rosie wreath,
Not so much honoring thee,
As giving it a hope, that there
It could not withered be.
But thou thereon did'st onely breathe,
And sent'st it back to mee:
Since when it growes, and smells, I sweare,
Not of it selfe, but thee.
Robert Burns: The Poetry (1896)
--------------------------------------------------------------
One Perfect Rose
A single flow'r he sent me, since we met,
All tenderly his messenger he chose;
Deep-hearted pure, with scented dew still wet - -
One perfect rose.
I know the language of the floweret.
“My fragile leaves,” it said, “his heart enclose.”
Love long has taken for his amulet
One perfect rose.
Why is it no one ever sent yet
One perfect limousine, do you suppose?
Ah no, it's always just my luck to get
One perfect rose.
Dorothy Parker
--------------------------------------------------------------
It's More Than Saying I Love You
We give on this day candy and flowers,
But we never stop to say thank you for the many hours.
You have stood by my side and gave a smile,
As if to tell our hearts it's been worth every mile.
No need to buy a teddy bear or even a card,
It's pretty simple and not at all hard.
Just put your arms around me and hold me tight,
And say without words that in your heart all is right.
You may say I Love You throughout the year,
But on this day you need to make sure.
The words so sweet and straight from your heart,
That your life would be lonely without my part.
So put forth the effort and take the time,
Look me in the eye and say I'm glad you're mine.
Marai
Friday, February 13, 2009
Whats the LOVE Says about the Love!
Thursday, February 12, 2009
DON

DON Ke Phone Ka Intzaar To 11 college ki ladkiya kar rahi hai;
Par DON Ka Phone Aana Mumkin hi nahi Namumkin Hai.
Kyoki.....
DON ke Phone me Balance HI Nahi hai.
Wednesday, February 11, 2009
I am sitting in my office..........
Thinking hard about life
How it changed from a maverick collage life to strict professional life…...
How tiny pocket money changed to huge monthly paychecks
but then why it gives lesss happiness….
How a few local denim jeans changed to new branded wardrobe
but then why there are less people to use them
How a single plate of samosa changed to a full Pizza or burger
But then why there is less hunger…..
Here i am sitting in my office @ night…
Thinking hard about life
How it changed…..
How a bike always in reserve changed to bike always on
but then why there are less places to go on……
How a small coffee shop changed to cafe coffee day
but then why its feels like shop is far away…..
How a limited prepaid card changed to postpaid package
but then why there are less calls & more messages……
Here i am sitting in my office @ night…
Thinking hard about life
How it changed…..
How a general class journey changed to Flight journey
But then why there are less vacations for enjoyment….
How a old assembled desktop changed to new branded laptop
but then why there is less time to put it on……….
How a small bunch of friends changed to office mate
but then why after 8'o Clock it always feel like getting late….
Here i am sitting in my office @ night…
Thinking hard about life
How it changed….. how it changed……..
See where your friends are with Google Latitude
With Google Latitude, a new feature on Google Maps for mobile and a gadget for iGoogle coming out today, we're kind of turning that idea on its head, making the "where" matter again. Latitude allows you to see where your friends are located in real time on a map, anywhere in the world.

Use your Gmail account to join Latitude and you can specify which of your Gmail contacts can see your location. You can choose to automatically detect your best location, share city-level information only, set your location manually, or hide your location altogether. (To learn more about Google Latitude's privacy controls, check out this video.)
From within Latitude you can communicate with your friends via text message, Google Talk, Gmail, or a good old fashioned phone call. Your status messages and profile picture are synced with your Gmail account, so as you update them on the go, your Gmail contacts will see the changes in real time.
To try Google Latitude, go to google.com/latitude from your computer or your phone's mobile browser. Latitude is available on Android, Blackberry, S60, Winmo, and will be coming soon to the iPhone, through the Google Mobile App.
New in Labs: Multiple Inboxes
So when I heard about Gmail Labs, I started implementing a Labs feature in my 20% time that would help me (and you!) spend less time monitoring important messages that may end up getting filtered away. Starting today, you can try Multiple Inboxes, a Labs experiment which makes it possible to have more than one 'inbox' in your default Gmail view.
An image is worth a thousand words, so here's what my inbox looks like:

In addition to a quick view of my important labels, I also like to keep all my starred and draft messages in separate panels.
After you turn on Multiple Inboxes from the Labs tab under Settings, you can configure what you want to see, as well as set the number of messages displayed and the positioning of your panels from the Multiple Inboxes section under Settings.
However you choose to use it, let us know how we can improve the Multiple Inboxes experiment -- all feedback is welcome.
New in Labs: Offline Gmail
Today we're starting to roll out an experimental feature in Gmail Labs that should help fill in those gaps: offline Gmail. So even if you're offline, you can open your web browser, go to gmail.com, and get to your mail just like you're used to.
Once you turn on this feature, Gmail uses Gears to download a local cache of your mail. As long as you're connected to the network, that cache is synchronized with Gmail's servers. When you lose your connection, Gmail automatically switches to offline mode, and uses the data stored on your computer's hard drive instead of the information sent across the network. You can read messages, star and label them, and do all of the things you're used to doing while reading your webmail online. Any messages you send while offline will be placed in your outbox and automatically sent the next time Gmail detects a connection. And if you're on an unreliable or slow connection (like when you're "borrowing" your neighbor's wireless), you can choose to use "flaky connection mode," which is somewhere in between: it uses the local cache as if you were disconnected, but still synchronizes your mail with the server in the background. Our goal is to provide nearly the same browser-based Gmail experience whether you're using the data cached on your computer or talking directly to the server.
Offline Gmail is still an early experimental feature, so don't be surprised if you run into some kinks that haven't been completely ironed out yet. We've been using offline Gmail internally at Google for quite a while (I've read thousands of messages and answered hundreds en route to visit my son and my daughter). And it's saved me more than once when my home network connection ran into issues (we have squirrels at home that love to chew through outside cable wires). Now we're ready to have a larger set of people try it out, so we're making it available in Gmail Labs for those of you who want to test out Gmail's latest and greatest and send us your feedback.
We're making offline Gmail available to everyone who uses Gmail in US or UK English over the next couple of days, so if you don't see it under the Labs tab yet, it should be there soon. Once you see it, just follow these steps to get started:
- Click Settings and click the Labs tab.
- Select Enable next to Offline Gmail.
- Click Save Changes.
- After your browser reloads, you'll see a new "Offline0.1" link in the upper righthand corner of your account, next to your username. Click this link to start the offline set up process and download Gears if you don't already have it.
Saturday, February 7, 2009
Atal Bihari Vajpayee| अटल बिहारी वाजपेयी | I wish you for good Health

I wish you Health…
So you may enjoy each day in comfort.
I wish you the Love of friends and family…
And Peace within your heart.
I wish you the Beauty of nature…
That you may enjoy the work of God.
13th & 16th Prime Minister of India
In office
May 16, 1996 – June 1, 1996
Preceded by P.V. Narasimha Rao
Succeeded by H.D. Deve Gowda
In office
March 19, 1998 – May 22, 2004
Preceded by I. K. Gujral
Succeeded by Manmohan Singh
Born December 25, 1924 (1924-12-25) (age 84)
Gwalior State, India
Political party Bharatiya Janata Party
Occupation Politician , Poet
Religion Hindu
Signature Atal Bihari Vajpayee's signature
Atal Bihari Vajpayee (Hindi: अटल बिहारी वाजपेयी, IPA: [əʈəl bɪhaːɾiː ʋaːdʒpeiː]) (born December 25, 1924) served as the thirteenth and sixteenth Prime Minister of India. After a brief stint as Prime Minister in 1996, Vajpayee headed a coalition government from October 13, 1999 until May 19, 2004. He has since retired from active politics, though as a Member of Parliament, he has at times commented on various issues.
Friday, February 6, 2009
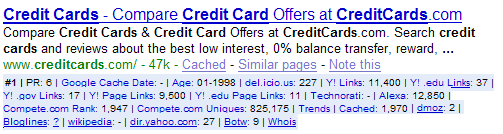
SEO Basics | Search Engine Optimization Made Easy
- users type what they want to find into search boxes, making search engines the most precisely targeted marketing medium in the history of the world
- once you gain traction in the search results the incremental costs of gaining additional exposure are negligible when compared with the potential rewards, allowing individuals and small businesses to compete with (and perhaps eventually become) large corporations
- market research
- keyword research
- on page optimization
- site structure
- link building
- brand building
- viral marketing
- adjusting
- staying up to date
Market Research
Do you have what it takes to compete in a market?
You can extend out the research you get from the search results by using the SEO for Firefox extension with the Firefox browser. This places many marketing data points right in the search results, and thus lets you see things like
- site age
- Google PageRank
- inbound link count
- if any governmental or educational sites link at their site
- if they are listed in major directories
- if bloggers link at their sites
Keyword Research
What keywords are people searching for?
Use the SEO Book Keyword research tool to search for popular and Long Tail keywords related to your industry. This tool cross references the Google Keyword Tool, Wordtracker, and other popular keyword research tools. Notice how our keyword tool provides daily search estimates and cross references other useful keyword research tools.
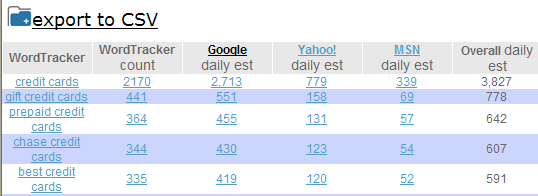
Keyword research tools are better at providing a qualitative measure than a quantitative measure, so don't be surprised if actual traffic volumes vary greatly from the numbers suggested by these tools. When in doubt you can also set up a Google AdWords account to test the potential size of a market.
In addition to looking up search volumes for what keywords you think are important also take the time to ask past customers how they found you, why they chose you, and what issues were important to them in chosing you.
You can also get keyword ideas by doing things like
- checking your web analytics or server logs
- looking at page contents of competing websites
- looking through topical forums and community sites to see what issues people frequently discuss
Site Structure
How should you structure your site?
Before drafting content consider what keywords are your most important and map out how to create pages to fit each important group of keywords within your site theme and navigational structure based on
- market value
- logical breaks in market segmentation
- importance of ranking in building credibility / improving conversion rates
- your most important categories or pages are linked to sitewide
- you link to every page on your site from at least one other page on your site
- you use consistant anchor text in your navigation
- you link to other content pages (and expeically to action items) from within the content area of your website
On Page Optimization
It is hard to rank for keywords that do not appear in your page content, so each page should be organized around the goal of ranking for a specific keyword phrase, with some related phrases and related keywords mixed into the page copy.
If possible create hand crafted meta description tags which compliment the page title by reinforcing your offer. If the relevant keywords for a page have multiple formats it may make sense to help focus the meta description on versions you did not use in the page title.
As far as page content goes, make sure you write for humans, and use heading tags to help break up the content into logical sections which will improve the scanability and help structure the document. When possible, make sure your page content uses descriptive modifiers as well.
Each page also needs to be sufficiently unique from other pages on your site. Do not let search engines index printer friendly versions of your content, or other pages where content is duplicate or nearly duplicate.
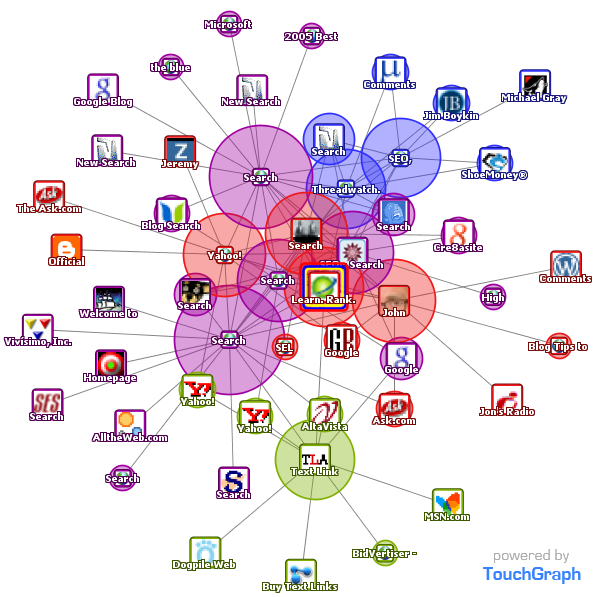
Link Building
Search engines view links at votes, with some votes counting more than others. To get high quality links (that help your site rank better) you need to participate in the social aspects of your community and give away valuable unique content that people talk about and share with others. The below Google TouchGraph image shows a small graphic representation of sites in the search field that are related to SeoBook.com based on linking patterns.
In this post Matt Cutts suggested that Google is getting better at understanding link quality. Search engines want to count quality editorial votes as links that help influence their relevancy algorithms.
- try to link to your most relevant page when getting links (don't point all the links at your home page)
- mix your anchor text
- use Yahoo! Site Explorer and other tools to analyze top competing backlinks
- don't be afraid to link out to relevant high quality resources
- submit your site to general directories like DMOZ, the Yahoo! Directory, and Business.com
- submit your site to relevant niche directories
- here is more background on directories and SEO
- if you have a local site submit to relevant local sites (like the local chamber of commerce)
- join trade organizations
- get links from industry hub sites
- create content people would want to link at
- here is a list of 101 useful link building strategies
Brand Building
Brand related search queries tend to be some of the most targeted, best converting, and most valuable keywords. As you gain mindshare people will be more likely to search for your brand or keywords related to your brand. A high volume of brand related search traffic may also be seen as a sign of quality by major search engines.
If you build a strong brand when people search for more information about your brand and other websites have good things to say about your brand, these interactions help reinforcing your brand image and improving your lead quality and conversion rates.
Things like advertising and community activity are easy ways to help improve your brand exposure, but obviously branding is a lot more complicated than that. One of my favorite books about branding is Rob Frankel's The Revenge of Brand X.
Viral Marketing
Link building is probably the single hardest and most time consuming part of an effective SEO campaign, largely because it requires influencing other people. But links are nothing but a remark or citation. Seth Godin's Purple Cow is a great book about being remarkable.
Measuring Results
Half the money I spend on advertising is wasted; the trouble is I don't know which half.
- John Wanamaker
Search engines follow people, but lag actual market conditions. It may take search engines a while to find all the links poiting at your site and analyze how well your site should rank. Depending on how competitive your marketplace is it may take anywhere from a few weeks to a couple years to establish a strong market position. Rankings can be a moving target as at any point in time
- you are marketing your business
- competitors are marketing their businesses and reinvesting profits into building out their SEO strategy
- search engines may change their relevancy algorithms
Keeping up to date
How do you track the changes in the SEO market? In my SEO tools I also offer Google Gadgets, which make it easy for you to embed keyword, competitive, and link research tools inside any webpage. You can track your ranking changes using this free keyword rank checker.
Best of luck with your sites!